The “We’re 18 months into a 2-month project” joke was getting old. So, here it is, the new wavemotiondigital.com, or, as it is now known, wmd.dev. This new site could not have been created without the wonderful WMD support crew and all of our clients. For the longest time we never focused on our own […]
Upgrading all CentOS 7 servers to AlmaLinux 9

Since RedHat decided to kill off the CentOS (Community Enterprise Operating System) and replace it with the Fedora releases we have been looking at alternative Linux operating systems to power our servers. We have been very happy with the efforts of AlmaLinux and Rocky Linux. Both are nearly identical, except for branding and both products […]
Matt Mullenweg calls WP Engine a ‘cancer to WordPress’ and urges community to switch providers

Updated 9/26/2024 Article: Matt Mullenweg calls WP Engine a ‘cancer to WordPress’ and urges community to switch providers We have know for a long time that WPEngine has been really good at marketing and not so good at providing a decent product. WP Engine has a long history of bait-and-switch tactics with their customers. We […]
Our post made a meme!

And no, we didn’t create it! Back in April we wrote about a lawsuit forcing Google to delete data collected while browsing using Incognito mode. While it is no surprise that Google keeps everything it collects to use for marketing this is just Fred unmasking the bad guy a la Scooby Doo (another great meme). […]
Google agrees to destroy browsing data collected in Incognito mode

They said the quiet part out loud. For a long time we have had little trust in Google. As the saying goes, “if something is free, you are the product” and that is especially true for one of the worst offenders when it comes to privacy. Google Docs, Sheets and Chrome are all great products […]
Vultr: Living up to their name, unacceptable TOS

This morning we received word of a new Terms of Service from one our infrastructure providers, Vultr, owned by Constant.com. Within their TOS they outline that they claim ownership of any content that is placed on their servers. An excerpt from the new TOS (which we have NOT agreed to) is below: ==== information, text, […]
The big deal about WMD DNS Passes
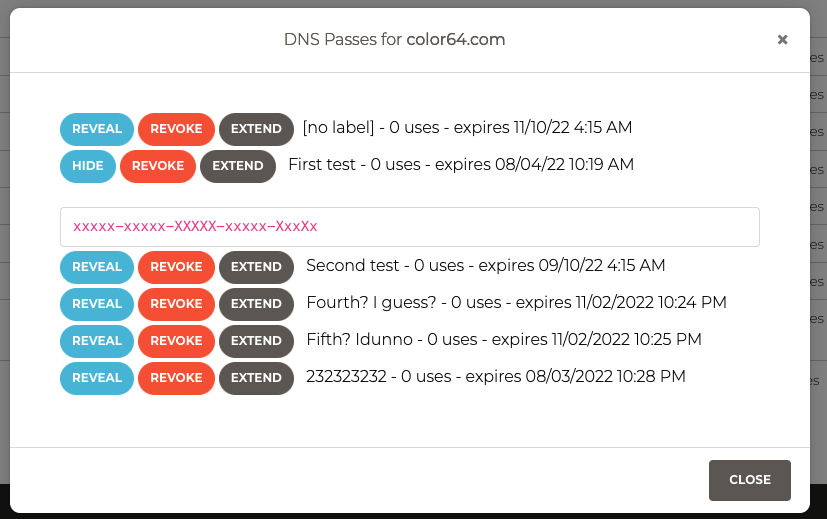
WMD’s DNS Manager We are very excited to debut our DNS manager system! This system allows you to manage DNS records regardless of where they are hosted. The need for this came about when editing DNS records became much more important to managing web services. See, some entities require verification of domain ownership by creating […]
Stating the obvious: You Can’t Trust Google
We have long preached about Google being a privacy vampire, finding any little way possible to monetize on every click you make. Why do you think so many of their services are “free” as in “cost no money”? Everything you put into Google is stored and your profile information is sold to whomever bids on […]
Connecting two domains in Zimbra for chat/autocomplete
We ran into a unique case recently where a client needed to connect two domains so they were essentially on the same domain. Let’s say one domain was DOMAIN_B.DEV and the other was DOMAIN_A.COM. What you are trying to do is make each domain’s GAL (Global Address Listing) available to each other. This must be […]
Fix macOS Ventura SSH access denied

The latest version of the Mac operating system, macOS 13 “Ventura” changes the way things are handled with OpenSSH. Certain legacy servers no longer adhere to the security policies of some servers that are running older OpenSSH software, specifically RedHat Enterprise Linux and CentOS Linux prior to version 7. There are a couple of ways […]
When something is free you are the product: Microsoft Edition

Microsoft purchased GitHub in 2018. For those who are not in-the-know, GitHub is a code repository that allows users to work collaboratively with their development team. It is a 3rd-party SaaS offering that offers a free tier and other pair tiers. Now GitHub Users Want to Sue Microsoft For Training an AI Tool With Their […]
